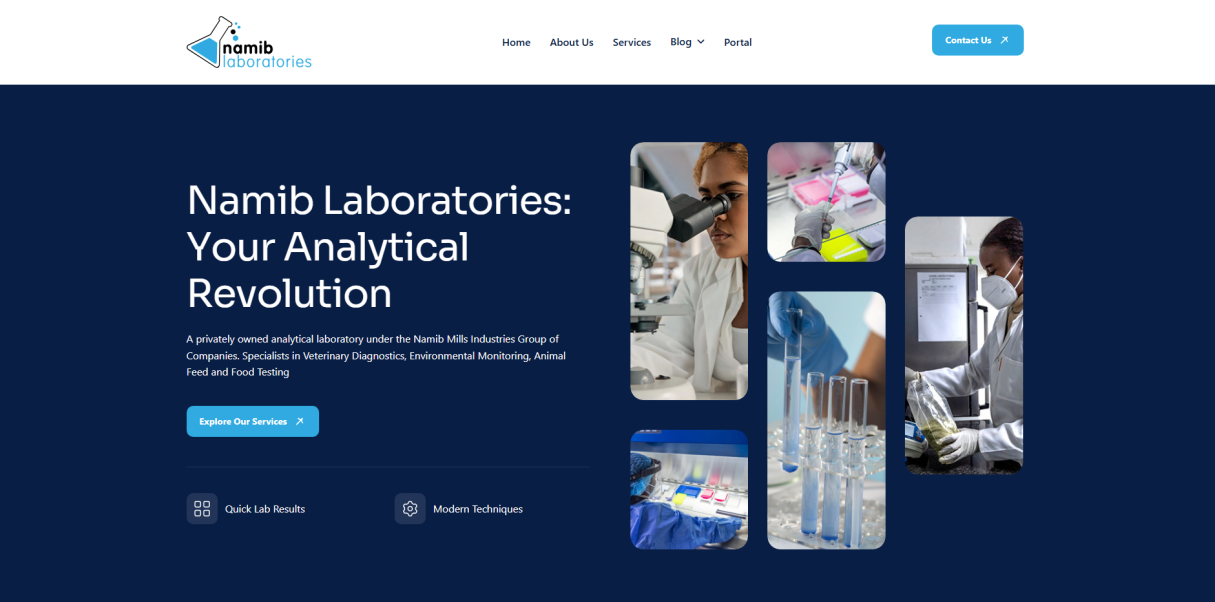
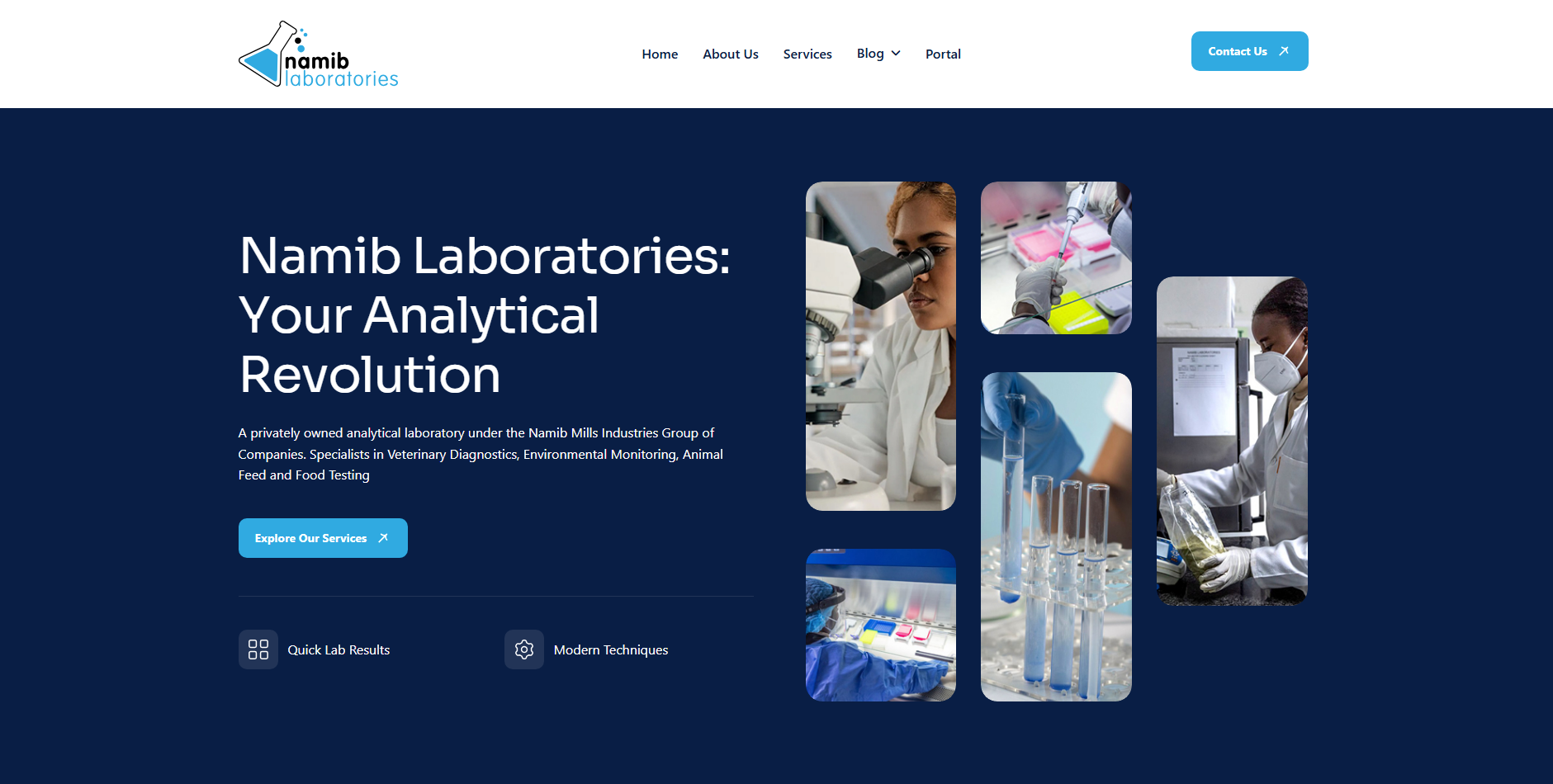
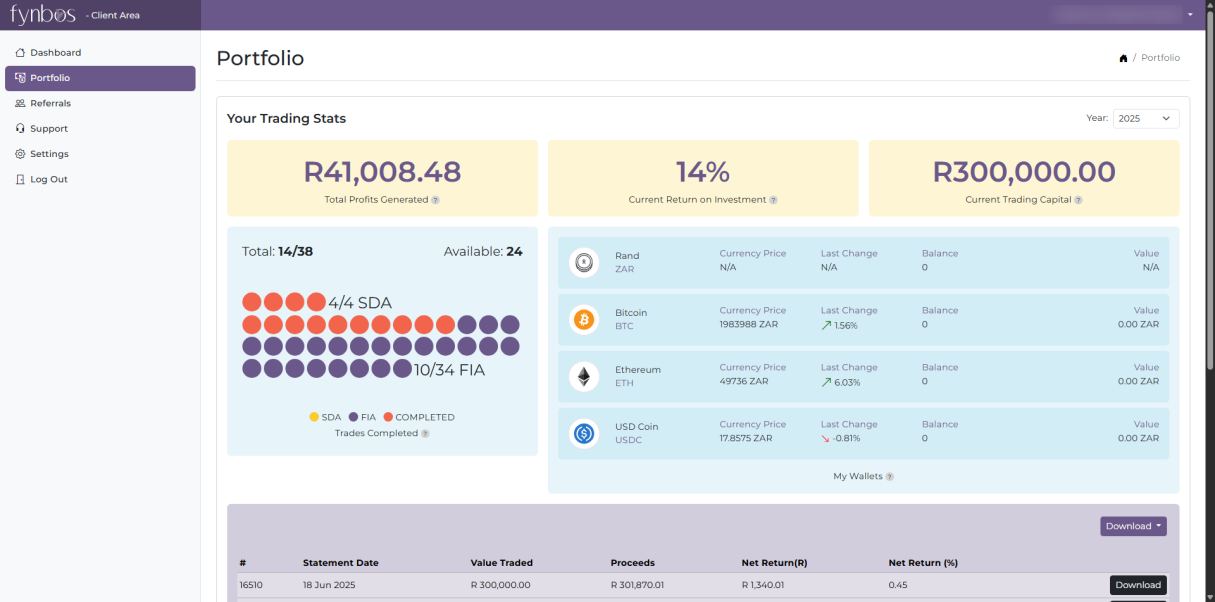
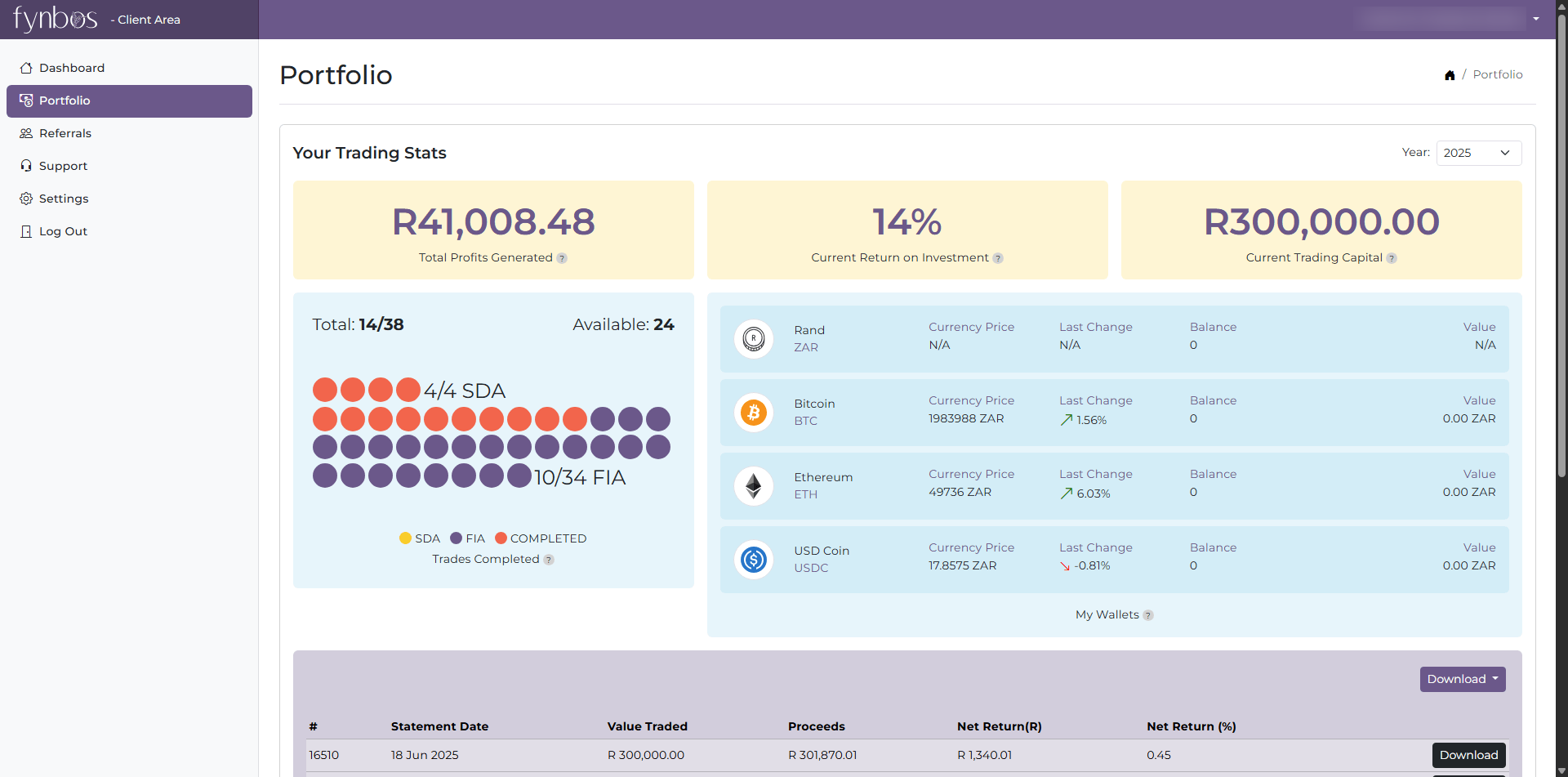
18+ years of experience securing servers, systems, and sensitive data.
We help businesses identify and eliminate security risks — before attackers find them. Our security stack includes infrastructure reviews, penetration tests, phishing simulations, vulnerability assessments, and hardening for Linux, Windows, and cloud environments.
Whether you're working toward compliance (like POPIA or GDPR) or simply want to sleep better at night, we’ll help you lock things down.
Penetration Testing & Ethical Hacking
We simulate real-world attacks and custom exploits to uncover weaknesses in your websites, apps, APIs, and servers. Every test includes a full report, technical remediation notes, and prioritized risks — reviewed with you in plain English.
Need retesting or compliance verification? We’ll keep your systems audit-ready and secure.
Server Hardening & OS Security
Our team performs in-depth reviews of Linux, Windows, and containerized environments. We configure firewalls, disable unnecessary services, enforce strong authentication, and ensure your systems follow CIS Benchmarks or similar best practices.
We also lock down SSH, automate patching, and monitor for unusual behavior.
Security Monitoring & Alerting
We implement lightweight, real-time monitoring tools to alert you to threats — before they escalate. From brute-force login attempts to suspicious network activity, our system-level alerts give you visibility and peace of mind.
For higher-tier clients, we offer custom dashboards, logs, and SIEM integrations.
Email, DNS & Application-Level Protection
Security isn’t just about servers. We help you configure SPF, DKIM, and DMARC for email protection, secure your DNS records, and lock down Laravel, WordPress, and custom apps with rate-limiting, firewalls, and secure coding practices.
Phishing Simulations & Team Awareness
Your employees are your biggest vulnerability. We offer realistic phishing simulations and awareness training to test how your team reacts to threats — and improve it over time. Each campaign includes reports, feedback, and repeatable playbooks.
Secure Development & Code Reviews
Already building your own software? We’ll review your codebase, database queries, and API endpoints for vulnerabilities — and help you adopt secure design patterns as you scale. Our Laravel and Node.js specialists focus on practical, non-blocking improvements that improve real-world resilience.